DSALTA Blog
How Secure Are the World's Top 100 Telecom Providers in 2025?

Written by
Ogulcan Ozdemir
|
Published on
Dec 11, 2025
Why We Created This Report
Global telecom infrastructure supports almost every part of modern life. It carries the world's data, enables critical services, and connects billions of people and devices. The sector's cybersecurity posture directly impacts economic stability and public safety.
DSALTA published the 2025 Telecom Risk Assessment Report to answer a simple question: How resilient are the largest telecom providers when viewed through an objective, data-driven lens?
Our team analyzed the Top 100 telecom operators across 12 global regions. This group represents nearly $2 trillion in combined annual revenue and includes integrated operators, mobile carriers, cable and broadband ISPs, tower companies, and specialized communication providers.
The goal of the report is to highlight clear patterns in external security posture, vendor exposure, domain maturity, and infrastructure risk. It gives decision-makers a way to compare themselves against global peers and to understand where the industry is heading.
What You'll Learn in This Report
The Global Telecom Security Landscape
Telecom providers operate on different scales and with very different architectures. This leads to a wide range of security outcomes.
The highest performers score in the low-to-mid 800s. Others fall into the mid-400s. These differences reflect architectural discipline, vendor control, and modernization efforts more than company size or revenue.
Broadband and cable ISPs tend to show more consistent security maturity than mobile operators or large integrated carriers. In many cases, simpler infrastructure leads to fewer inherited risks.
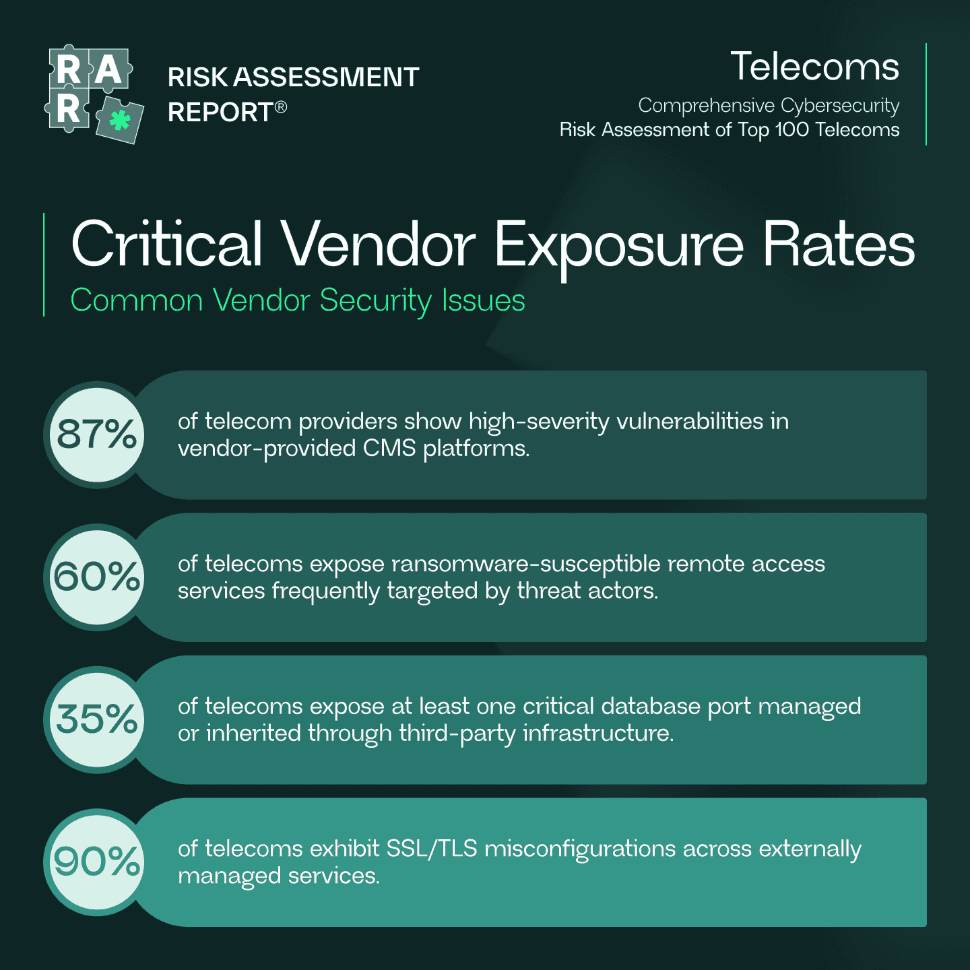
Vendor Risk: The Sector's Most Persistent Challenge
One theme stands out across all 100 telecoms we analyzed. Vendor-managed infrastructure creates concentrated and recurring exposure. The report includes several examples:
87% of telecoms have high-severity CMS vulnerabilities tied to external platforms
60% of exposed remote access services are frequently targeted by ransomware groups
35% have at least one critical database port exposed through third-party infrastructure or inherited configurations
90% show SSL and TLS weaknesses on services not directly operated by internal teams
These findings illustrate a pattern seen across many regions. Telecom providers are improving internal controls, yet they continue to inherit risk from vendors, cloud providers, and legacy outsourced infrastructure.
Learn more about managing vendor risk at scale and implementing continuous monitoring for third-party exposure.
Who Manages Vendor Exposure Well
Some telecoms demonstrate strong control over third-party environments. These providers maintain unified governance, limit public exposure, and enforce consistent baseline standards.
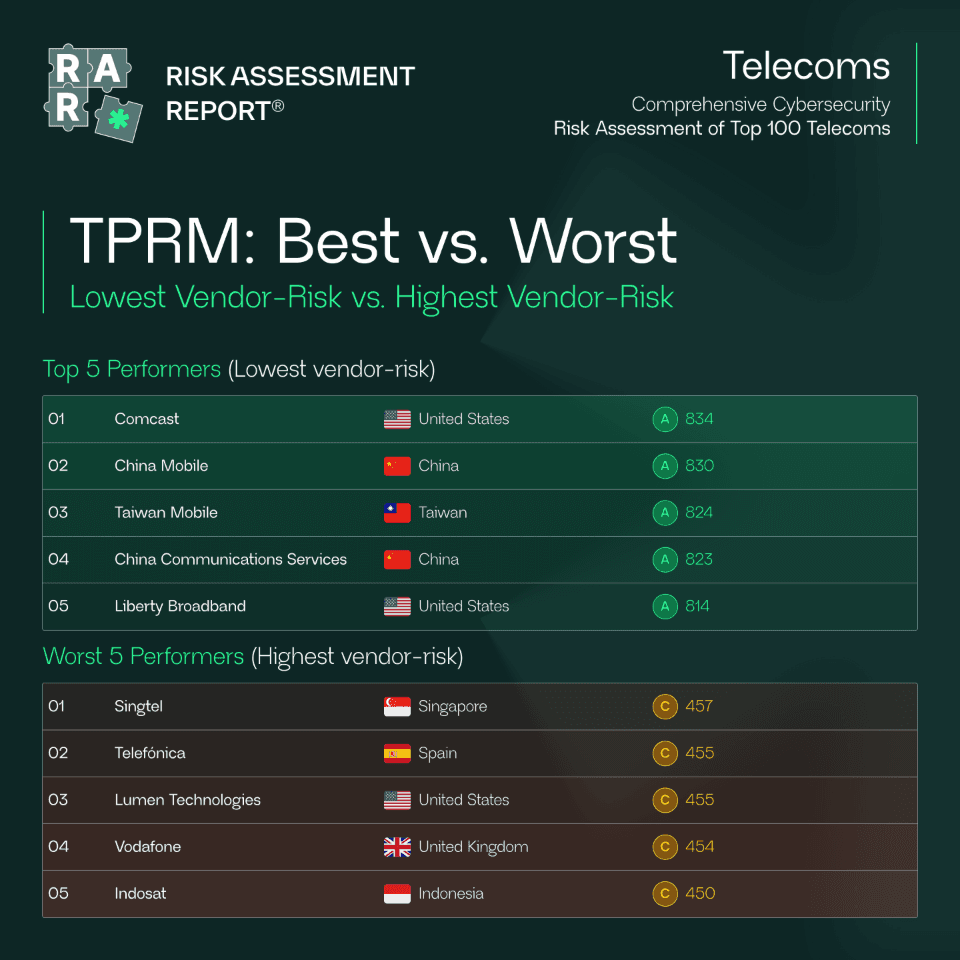
Lowest Vendor-Risk Telecoms
Comcast
China Mobile
Taiwan Mobile
China Communication Services
Liberty Broadband
These companies show that vendor complexity can be managed when security ownership and architecture are aligned.
Where Vendor Risk Creates the Most Pressure
At the opposite end of the spectrum, several telecoms struggle with older environments, multiple outsourced systems, and fragmented vendor ecosystems.
Highest Vendor-Risk Telecoms
Singtel
Telefónica
Lumen Technologies
Vodafone
Indosat
Their challenges often stem from inherited systems, regional expansion, and legacy outsourced infrastructure that were never modernized.
Segment Insights: Infrastructure Type Shapes Risk
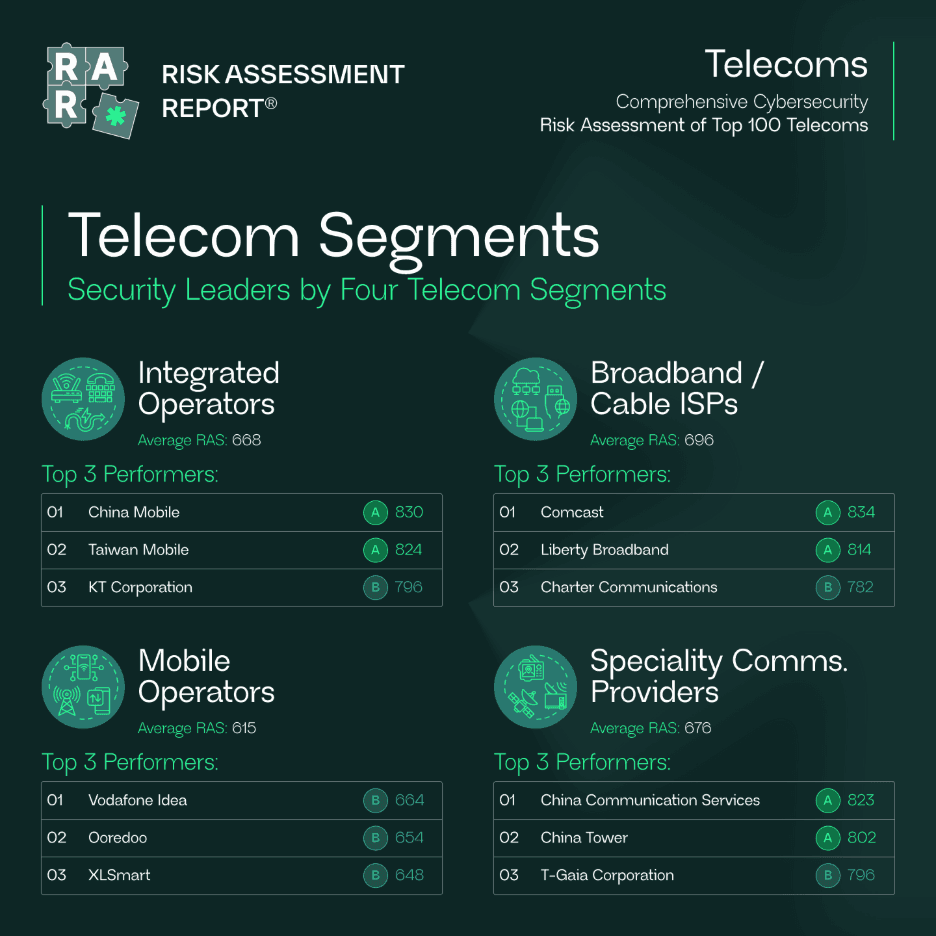
The report breaks down security outcomes across four telecom categories.
Integrated Operators
Broad portfolios and diverse infrastructure create uneven performance
Top performers: China Mobile, Taiwan Mobile, KT Corporation
Broadband and Cable ISPs
More consistent maturity due to stable networks
Top performers: Comcast, Liberty Broadband, Charter Communications
Mobile Operators
Higher exposure density and fragmented vendor relationships
Top performers: Vodafone Idea, Ooredoo, XLSmart
Specialty Communication Providers
Tower companies and backbone providers show strong discipline in focused domains
Top performers: China Communication Services, China Tower, T-Gaia Corporation
Why This Matters
Telecoms are not ordinary enterprises. They sit at the center of national communication networks and global digital infrastructure. A weakness in this layer can cascade across entire industries.
This year's report reinforces a clear point: Vendor ecosystems now shape telecom security posture as much as internal practices. As connectivity expands and third-party services become more embedded, transparency and measurable risk management become essential.
The RAR offers an evidence-based foundation for understanding where risk is concentrated and where leaders are pulling ahead.
Explore how DSALTA helps organizations automate vendor risk assessments and maintain continuous compliance across complex third-party ecosystems.
Access the Full Report
The complete 2025 Telecom RAR includes:
The full Top 100 RAS ranking
Detailed segment-level analysis
Ten-domain performance scoring
Regional and country-level summaries
Vendor exposure insights and parent-subsidiary comparisons
Actionable guidance for modernization and risk reduction
Download the 2025 Telecom Risk Assessment Report or contact research@dsalta.com for deeper analysis or enterprise-specific insights.




